Analysis of Remote Template Injection used by APT
EXECUTIVE SUMMARY
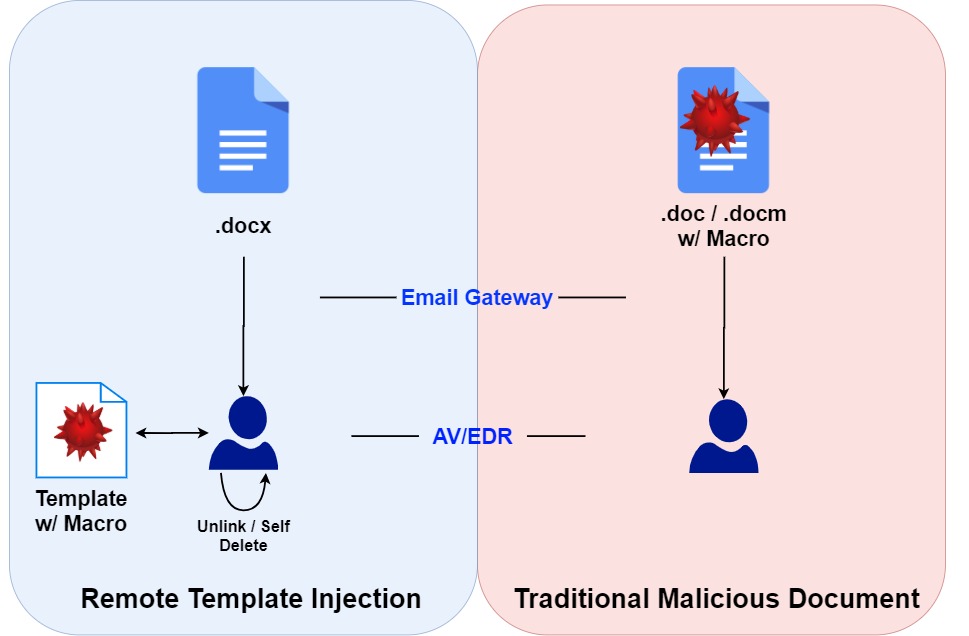
Attackers are continually trying to find new ways to target users with malware sent via email.Typically,
malicious Word documents that are sent as attachments to phishing emails will themselves contain a script or macro that executes malicious code
to get initial access. There are numerous techniques used on these malicious docs to bypass anti-virus detection (VBAStomping, obfuscation,
etc.). One such method is Remote Template Injection.
TECHNICAL INVESTGATION
Remote template injection was initially found in 2017 , later used by many APT's such as Gamaredon , Lazarus and many more .It was also listed on MITRE (T1221)